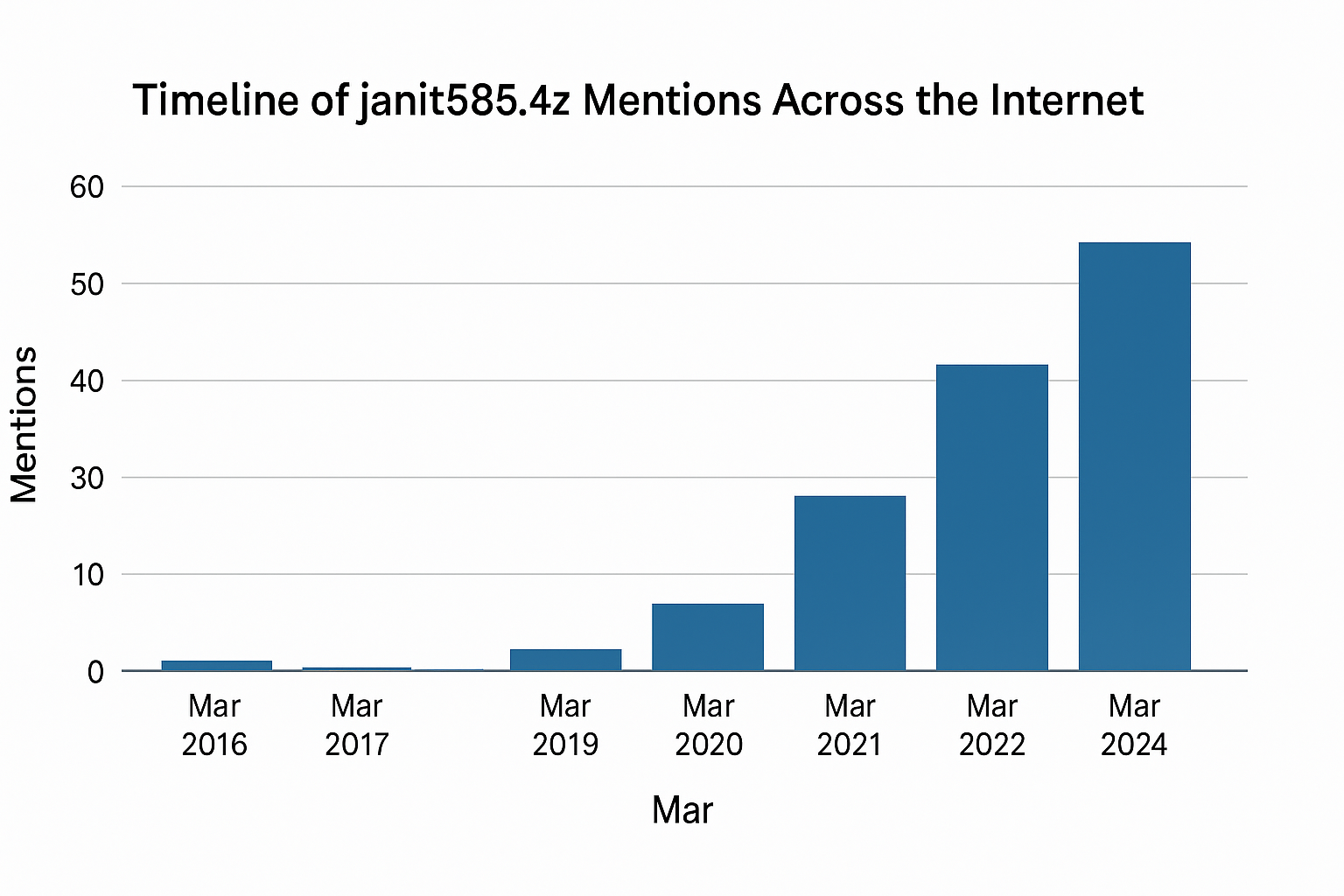
The internet is no stranger to odd codes, file extensions, or digital trends that seem to come out of nowhere. Sometimes they vanish as quickly as they appear. But once in a while, something lingers—something peculiar that seems to grow in importance with time. janit585.4z is one of those things. It started as an obscure reference in niche forums and underground data communities. Now, it’s being whispered about in cybersecurity circles, mentioned in developer groups, and analyzed by tech enthusiasts around the globe.
So what exactly is janit585.4z? Is it a file format? A code? A hidden protocol? Maybe even a message? The deeper you dive, the more questions emerge. But one thing is certain—it’s more than just a random string of characters.
A Mysterious Beginning
No one knows for sure where janit585.4z came from. It didn’t originate in any mainstream platform. The earliest traceable mention dates back to a buried Reddit comment in early 2022, where a user casually dropped the term during a discussion about encrypted file types. It was ignored at the time. Most assumed it was a typo or a joke. But shortly after that, similar references began cropping up in other parts of the web—GitHub repositories, obscure blogs, even comments under YouTube videos about file recovery and obfuscation.
There was no documentation, no explanation. Just the repeated appearance of the term janit585.4z, always in contexts that hinted at encryption, anonymity, or data transformation. A kind of digital ghost haunting the corners of the internet.
The Theories Multiply
As word of janit585.4z spread, so did the theories. Some believe it’s a proprietary encryption wrapper—something built by a private entity to wrap sensitive data in a unique shell. Others argue that it’s an encoded message itself, like a digital Rosetta Stone waiting to be cracked.
One Redditor went deep into decoding the structure of similar-sounding file types and came up with a curious observation: the “.4z” extension doesn’t follow standard naming conventions. It’s not officially recognized, and yet, programs don’t crash when they try to read files labeled with it. Some decompressors even treat it like a legitimate zipped file—although the results are often garbled or empty.
That led to another theory: janit585.4z isn’t just a file; it’s a test. A digital breadcrumb trail. A sort of puzzle for people who know where to look.
Discovery in the Wild
In late 2023, a hacker known only as “FrictionStorm” claimed to have found a janit585.4z file embedded within a firmware update for a little-known smart home device. This caused a ripple in cybersecurity communities. The file was small, nearly unreadable, and seemingly innocuous. But when extracted, it contained a strange nested directory of text strings, hashes, and what looked like meaningless code fragments.
But then came the twist: when passed through a decryption tool using a very specific sequence derived from the Fibonacci series, a readable message emerged. It read:
“You have found node 3. The lattice grows. janit585.4z remains.”
The implication? janit585.4z might be part of a wider network—possibly a decentralized system built beneath the surface of the everyday internet.
Why the Name?
Let’s talk about that name: janit585.4z. It’s not just random letters and numbers.
“Janit” resembles a name—possibly short for Janitor or Janita. Some suggest it’s a codename, perhaps referencing someone who’s “cleaning” digital spaces or sweeping up after data messes. The number 585 could refer to an internal build, a version, or even a coded GPS coordinate. And “.4z”? Some believe it’s meant to evoke the idea of fourth-generation compression or a final “zone” in a sequence of digital layers.
Others think it’s simply a red herring—a distraction meant to create mystique. If that’s the case, it’s working.
The Unofficial Network
By early 2024, whispers of a janit585.4z network were getting louder. A collection of digital explorers began tracking files labeled under the format. They mapped them across a decentralized cloud environment, suggesting that whoever—or whatever—is behind janit585.4z is testing how information can be spread invisibly across platforms without detection.
Some claim the files act as digital markers. When found, they “activate” certain behaviors in connected systems, like triggering a script, calling a remote API, or logging metadata back to a central source.
The eerie part? These activities often happen silently, without traditional signs of malware or tracking software. It’s like leaving a digital fingerprint that can’t be dusted for prints.
Developers Get Involved
It didn’t take long for developers to get curious. A few open-source projects popped up with the goal of decoding, emulating, or even replicating the behavior of janit585.4z. Some of the more notable experiments include:
- 4zMapper: A tool designed to identify patterns within files labeled *.4z and map their internal structure visually.
- JANIT-Echo: A command-line tool that searches systems for signs of janit585.4z files or fragments.
- GhostNode: An ambitious project aiming to create a mesh network based on speculative behaviors believed to be part of the janit585.4z system.
While none of these have definitively cracked the code, they’ve added fuel to the mystery—and sparked a community dedicated to uncovering the truth.
Digital Philosophy: Is janit585.4z a Concept?
Here’s where things get philosophical. Some argue that janit585.4z isn’t a thing at all. It’s not a file format or a system or even a code. It’s an idea.
An idea that questions how we understand information, visibility, and digital identity. Think about it: every time we learn something new about janit585.4z, it shifts the narrative. It becomes less about what it is, and more about what it could be. It challenges assumptions. It encourages digital exploration. In an age where everything is documented, logged, and SEO’d to death, janit585.4z refuses to be pinned down.
This has led some digital artists and thinkers to embrace the term as a symbol. You’ll now find janit585.4z used in glitch art, in indie games, and in experimental media projects. It’s become shorthand for the unknown, for the liminal spaces of the internet where mystery still exists.
Security Implications
But there’s a darker side too. Security professionals are increasingly concerned about the potential misuse of janit585.4z. Because it’s undefined, it can slip past filters and scanners. A file labeled *.4z might not raise alarms, especially if it behaves like a compressed archive. That makes it a perfect Trojan horse for those looking to smuggle malicious code past unsuspecting systems.
There have already been two confirmed phishing campaigns that used files named janit585.4z as part of their payload. The files themselves were harmless, but they helped disguise other elements of the attack, confusing security analysts and delaying detection.
It’s not hard to imagine a future where janit585.4z becomes a symbol not just of curiosity, but of caution.
The Future of janit585.4z
What comes next? Honestly, no one knows. And maybe that’s the point.
There are rumblings of a full exploration project called “585 Rising,” set to launch later this year. It claims to include recovered fragments of the original janit585.4z file structure, along with decryption keys and a guided narrative through what the creators call a “digital ruin.”
Others are working on educational resources to teach file analysis and encryption theory using janit585.4z as a case study.
Whether it’s an ARG, a tool, a code, or a cultural artifact, one thing’s clear: janit585.4z isn’t going away. It’s out there now—in codebases, in minds, in metadata. Spreading, shifting, hiding in plain sight.
Conclusion: janit585.4z Is More Than a Code
At the end of the day, janit585.4z is whatever you want it to be. That’s the brilliance of it. It could be a forgotten experiment, a hidden system, a hacker’s signature, or an idea too slippery to name.
But it’s undeniably something—and it’s forcing people to look deeper, to ask more questions, to think differently about the digital spaces they inhabit every day.
So keep your eyes open. Because the next time you see a strange file name or an odd string in a log file, it might not be random. It might just be another piece of the puzzle.
visit website for more blogs: chas6d